What is face recognition?
Discover the world of face recognition!
This interactive guide on facial recognition will enable you to understand the ins and outs of a technology that has evolved a lot since its inception and that lets us solve multiple problems and use cases today, thanks to artificial intelligence.
Index
Use this index to navigate through the guide:
What is face recognition and what is it for
Authentication beyond passwords
Ethics, bias and accessibility
The artificial intelligence dialectic
Introduction
Over the past fifty years, the unstoppable acceleration of technological development has completely transformed society. The hyper-connectivity enabled by the deployment of communications networks is allowing the digitisation of a significant part of our activities, bringing numerous benefits as well as some risks that need to be addressed. In this analogue-digital duality, one of the processes that remains key to providing security is identity verification.
Over the past fifty years, the (seemingly limitless) acceleration of technological development has completely transformed our societies. The hyperconnectivity driven by the expansion of communication networks is enabling the digitisation of a significant part of our activities, bringing numerous benefits but also certain risks that must be addressed. Within this analogue–digital duality, one of the processes that remains crucial in ensuring security is identity verification through facial recognition.
The meeting point between two worlds
In the physical world, this is a task we carry out on a daily basis intuitively, recognising people at a glance. When this same (by no means trivial) activity must be carried out automatically without human intervention, it is necessary to deploy all technological potential to obtain reliable results.
In this sense, biometrics in conjunction with artificial intelligence technologies form a robust team that allows us to provide security to digital processes where it is necessary to verify a person’s identity with guarantees.
The aim of this guide is to provide an informative review of the fundamental aspects of facial recognition systems, helping to understand their key points and most interesting applications as well as the most relevant challenges we have to address.
Terminology
Artificial Intelligence: is intelligence demonstrated by machines, unlike the natural intelligence displayed by humans and animals, which involves consciousness and emotionality. Leading AI textbooks define the field as the study of “intelligent agents”: any device that perceives its environment and takes actions that maximize its chance of successfully achieving its goals. (Source: Wikipedia)
Machine Learning: Machine learning is a branch of artificial intelligence and refers to the process by which computers develop pattern recognition or the ability to continuously learn and make predictions based on data, and then make adjustments without being specifically programmed to do so. (Source: hpe)
Deep Learning: A branch of machine learning. Unlike traditional machine learning algorithms, many of which have a finite learning capacity regardless of how much data they acquire, deep learning systems can improve their performance by being able to access more data, or in other words, make the machine more experienced. (Source: NetApp)
Neural Networks: One of the families of deep learning algorithms, inspired by the way neurons in our brains work. (Source: Luca)
Convolutional Networks: Are deep learning algorithms that are designed to work with images, taking them as input, and assigning importance (weight) to certain elements in the image in order to differentiate one from another. (Source: BootcampAI)
What is face recognition? How does it work?
Facial recognition is the process of automatically identifying a person’s identity through the analysis of an image of their face. This process encompasses a series of intermediate tasks ranging from the capture of the digital image to the final decision regarding the identity being analysed.
To cover all workflow stages it is necessary to make use of different technologies, among which biometrics and machine learning are key elements:
Biometrics
Biometrics is the set of techniques that, through the analysis of physical features (voice, iris, fingerprint, vein pattern, DNA, etc.) or behavioural ones (signature, gait, interaction with digital interfaces, etc.), make it possible to determine a person’s identity. Not all biometric features are equally easy to capture, nor do they provide the same level of reliability, so it is necessary to establish a compromise between these two factors, taking into account the requirements of the final system.
Machine Learning
Machine learning is a branch of artificial intelligence that seeks to make machines capable of making decisions in situations for which they have not been explicitly designed. The problem of biometric identity verification can be tackled purely from the point of view of machine learning algorithms, since it is always necessary to face new examples (new identities) on the basis of a previous training process.

Face recognition: A bit of history
It is not easy to define a single milestone for the beginning of the research and development of face recognition solutions, but there is some general consensus to consider Woodrow Wilson Bledsoe’s work in the early 1960s as the starting point.
His approach consisted of recording the spatial coordinates of facial points of reference on a RAND tablet in such a way that a face was characterised by a set of numerical data. When performing an identification process, the biometric features of the input image were compared with those previously stored in the database, so that it was possible to return the one that had the closest similarity.
Although the results were obviously limited by the capabilities of the hardware at the time, these studies determined that facial biometrics was a useful method for identity verification and laid the foundations for the basic workflow in a biometric system: capture, modelling and matching.
Over the next twenty years, progress was slow, limited to an increase in the number of facial features extracted (always anthropometric in nature). It was not until the late 1980s when it was possible to model a facial image in a more robust way.
Algebra methods and the development of machine learning algorithms
Sirovich and Kirby applied linear algebra methods to achieve low-dimensional facial representations, i.e. to reduce the most important features of a face to a small set of numerical values.
This work was extended by Turk and Pentland to apply it to the face detection process, thus opening the door to a fully automatic face recognition process (without the need to provide a previously cropped facial image).
From that moment on, research activity focused on two main lines: on achieving robust facial descriptors and developing machine learning algorithms that would make it possible to find patterns and criteria for distinguishing between these characteristics in order to differentiate between identities.
Facial recognition systems were successfully deployed in situations where it was necessary to automatically verify a person’s identity (such as access control), as well as serving as an alternative to the use of traditional passwords.
Impact of deep learning and neural networks
Even so, the key factor behind the significant improvement in the performance of biometric systems has been the explosion of deep learning technologies, which have brought about a genuine paradigm shift and an almost unanimous adoption across the industry.
From an ontological standpoint, deep learning algorithms represent a subset within machine learning, comprising various techniques aimed at obtaining high-level abstractions through the analysis of complex relationships among large sets of input data.
A fundamental component of deep learning is the neural networks, algorithms with a long history that have gained renewed relevance thanks to the exponential increase in computing power and the availability of vast amounts of data.
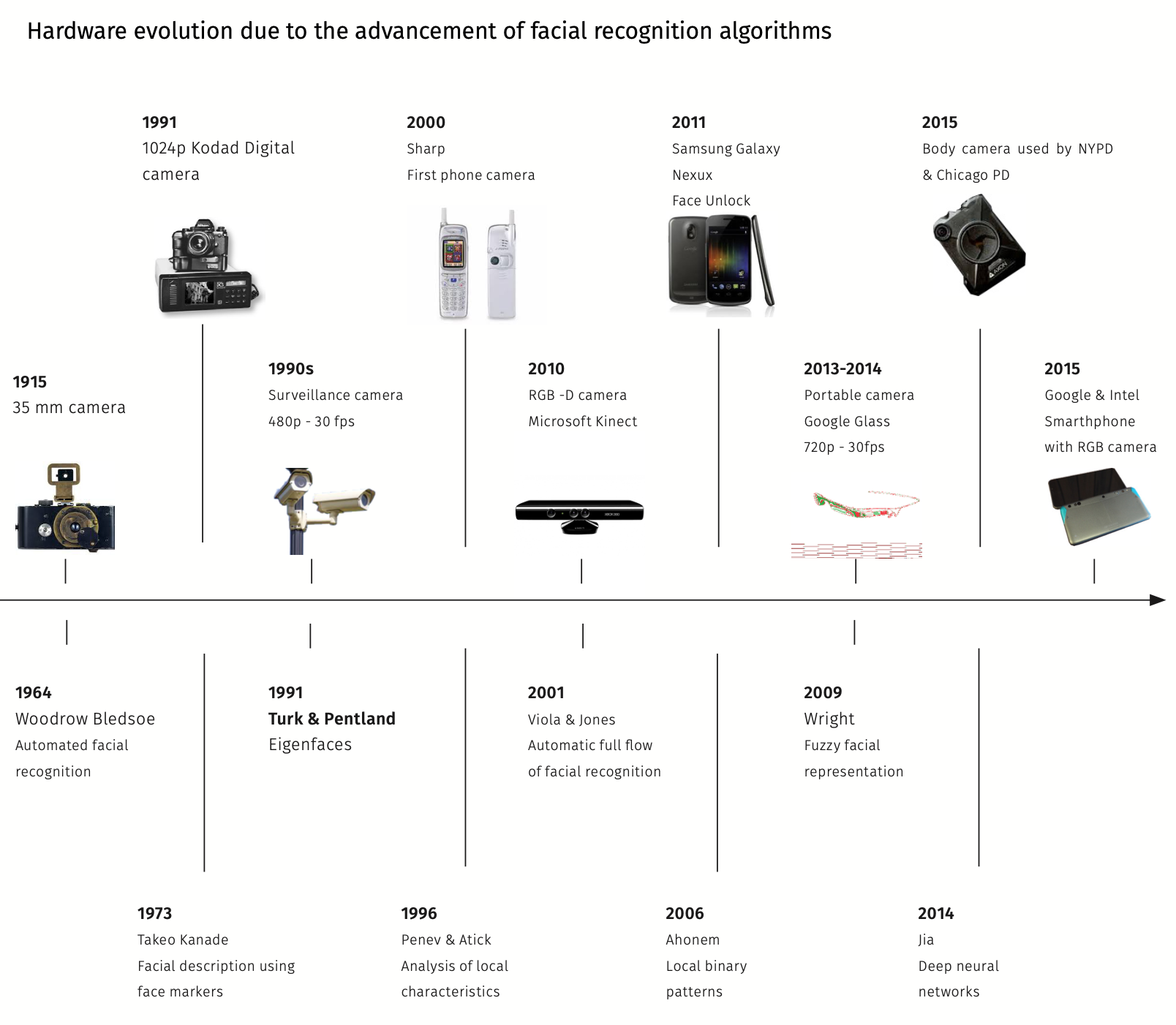
Figure 1: Hardware evolution linked to the development of face recognition algorithms.
The core of a face recognition system
As noted above, from a functional point of view, a face recognition system contains a number of distinct phases that allow the process to be successfully completed:
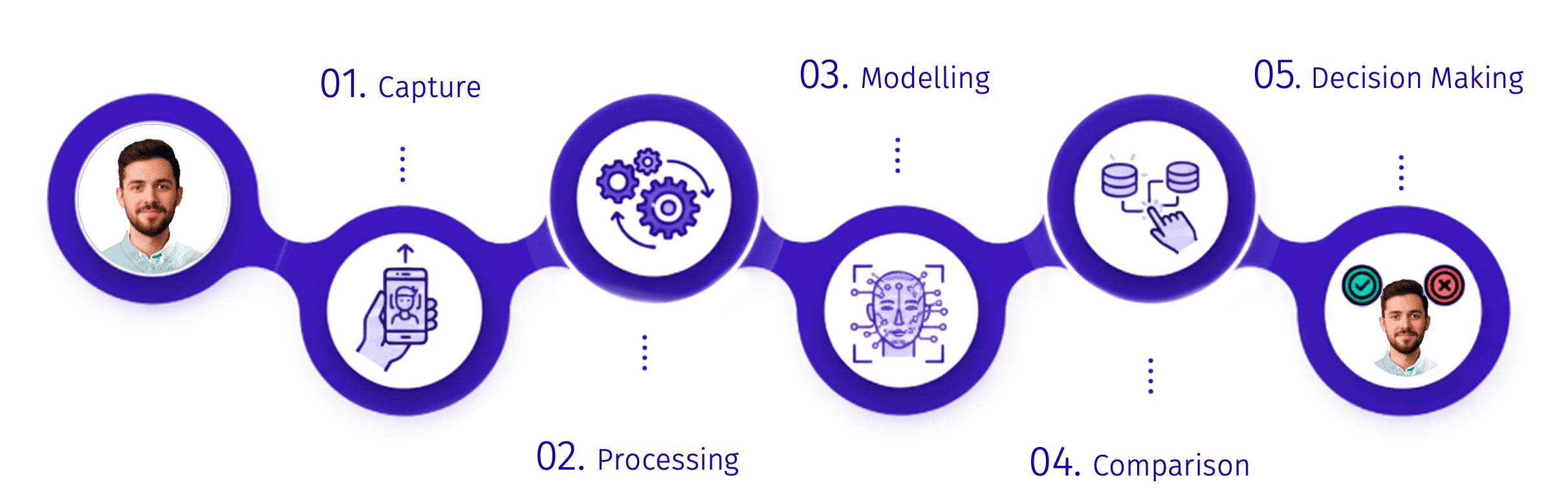
1. Capture
The beginning of the workflow is to obtain the basic information. In our case this information is just the face portion of the input image, so the first automatic process will be face detection. In recent years, intensive work has been carried out in the field of face detection algorithms, currently obtaining really high effectiveness rates even in the most demanding environments: artificial lights, very distant positions, use of glasses or masks. The result of this functional block will be a crop of the area of interest from the input image, so that the system can work from that moment onwards exclusively with the relevant information (the facial area).
2. Processing
In any system based on machine learning, processing is a fundamental stage. The objective is to normalise the input data within pre-established parameters so that the performance of the subsequent algorithms is optimal.
Machine learning systems use the conclusions drawn from the analysis of the training set to make decisions about new examples in production environments. For this reason, the input data must move within parameters similar to those used during training, avoiding extreme cases that could lead to undesired results.
In the case of a face recognition system, the processing consists of normalising the input image from the point of view of:
- Numerical values (illumination, colour deviations, range of coding values, etc.).
- Content (centring the position of the face around a symmetry axis thanks to the localisation of key facial points).
3. Modelling
This is the key operation in the overall process as it transforms an input image (the output of the processing block) into a set of numerical values commonly known as a feature vector or biometric template.
A feature vector could be understood to be a robust encoding of the most significant aspects of a face that differentiates it from other faces.
Artificial intelligence algorithms analyse complex patterns in the input data to locate the features with the highest discriminative power and use them to model an input image.
Currently the feature extraction process is mostly carried out by deep learning algorithms (usually convolutional network architectures), as they are able to find very complex (non-linear) relationships in the input data, far outperforming manual feature extractors used in the previous generation.
4. Comparison
Once the feature vector associated with a facial image is obtained, it is possible to undertake the comparison process. The objective is to determine the resemblance (in numerical terms) between faces in order to implement one of the following biometric operations:
- Verification: is it me? Given an input image and an identity tag, the system must determine whether the person is really who they claim to be by analysing the resemblance between the input image and another previously stored in the system. This operation therefore requires a prior registration process.
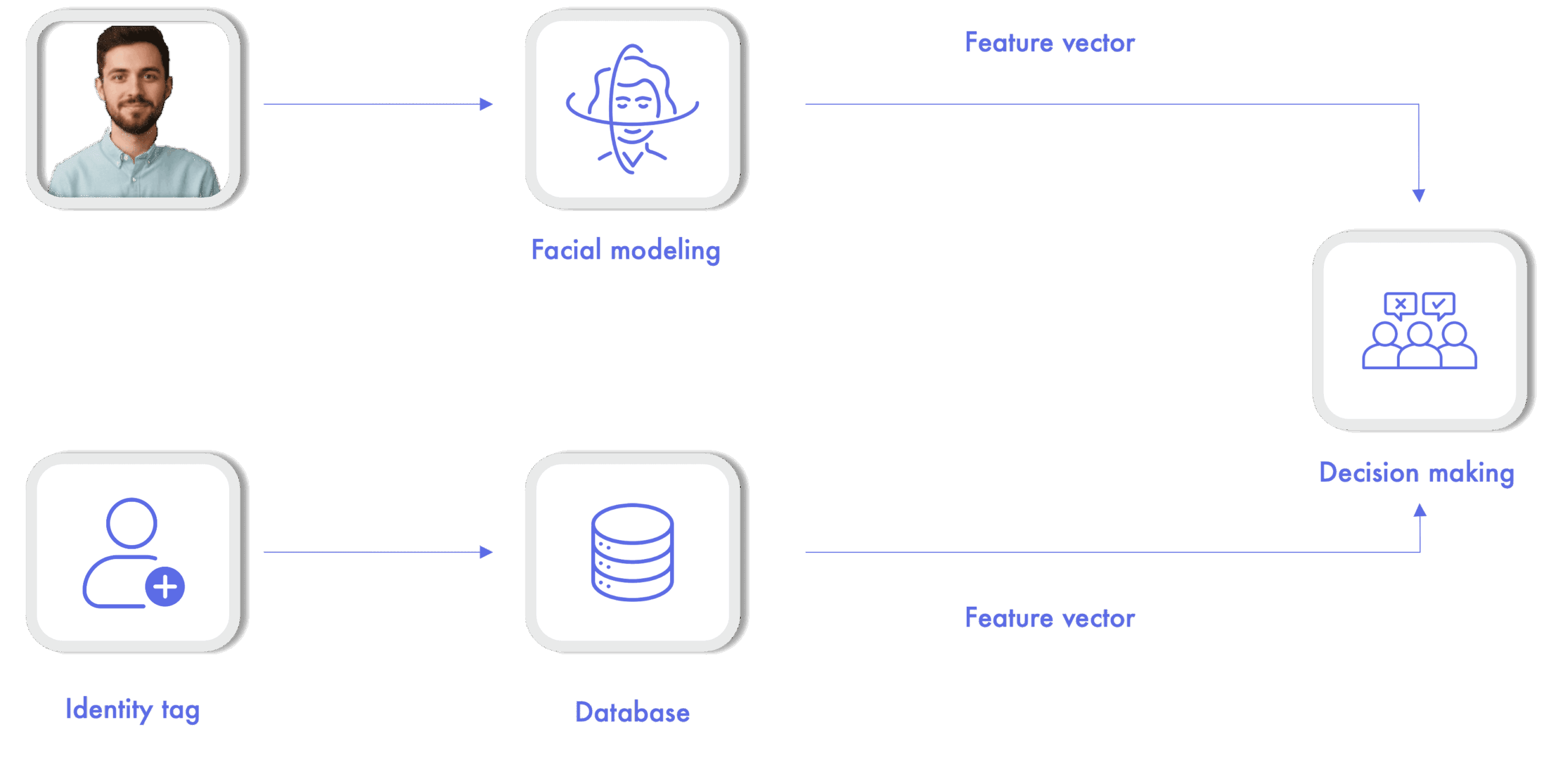
- Identification: who am I? Given an input image, the system shall determine the identity of the user by comparison with a set of previously registered people.
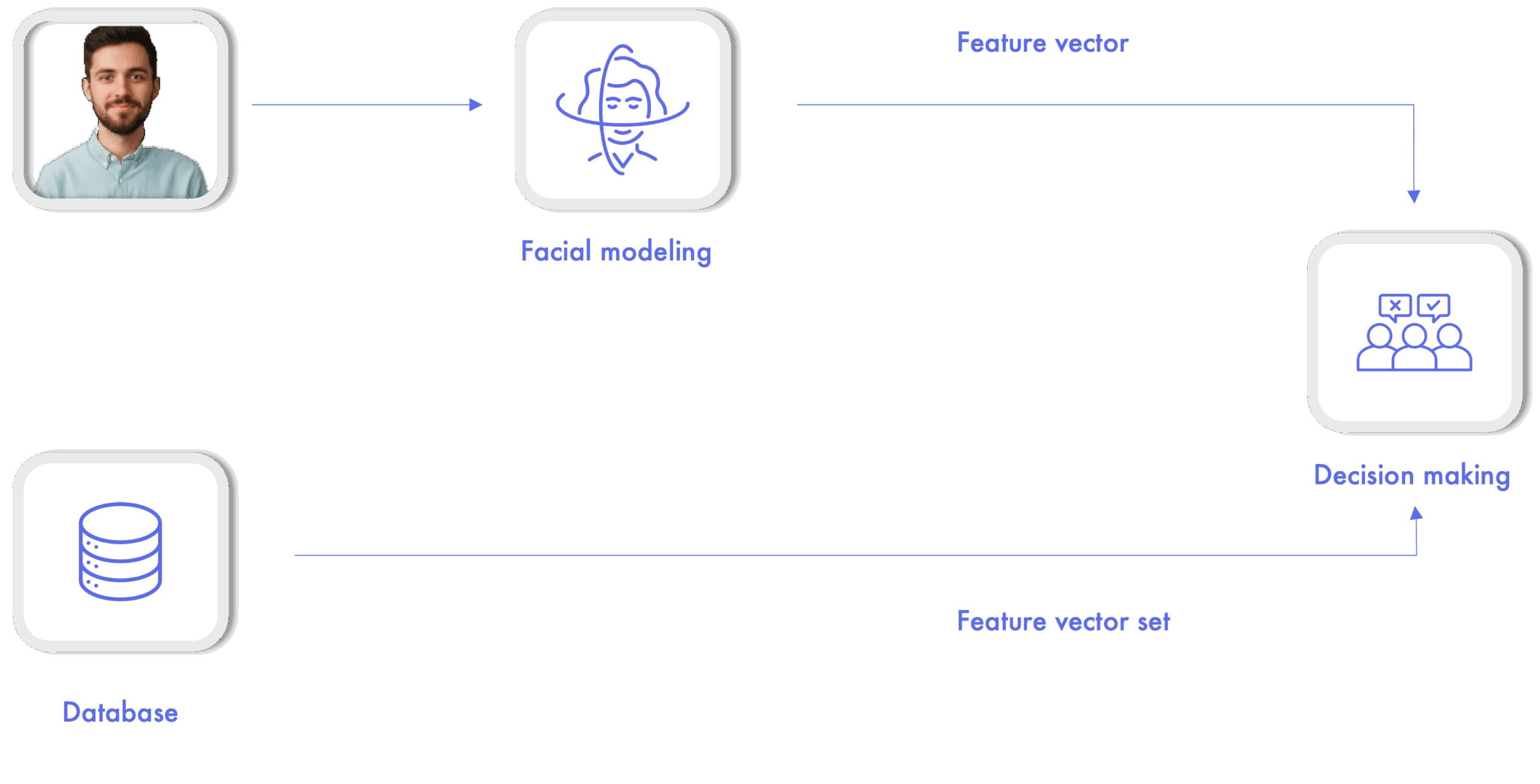
- Matching: are they the same person? Given two input images, the objective is to determine the match between them. A common use of this operation is in remote customer registration systems, where the image of an identity document is compared with an image taken from the user during the registration process.
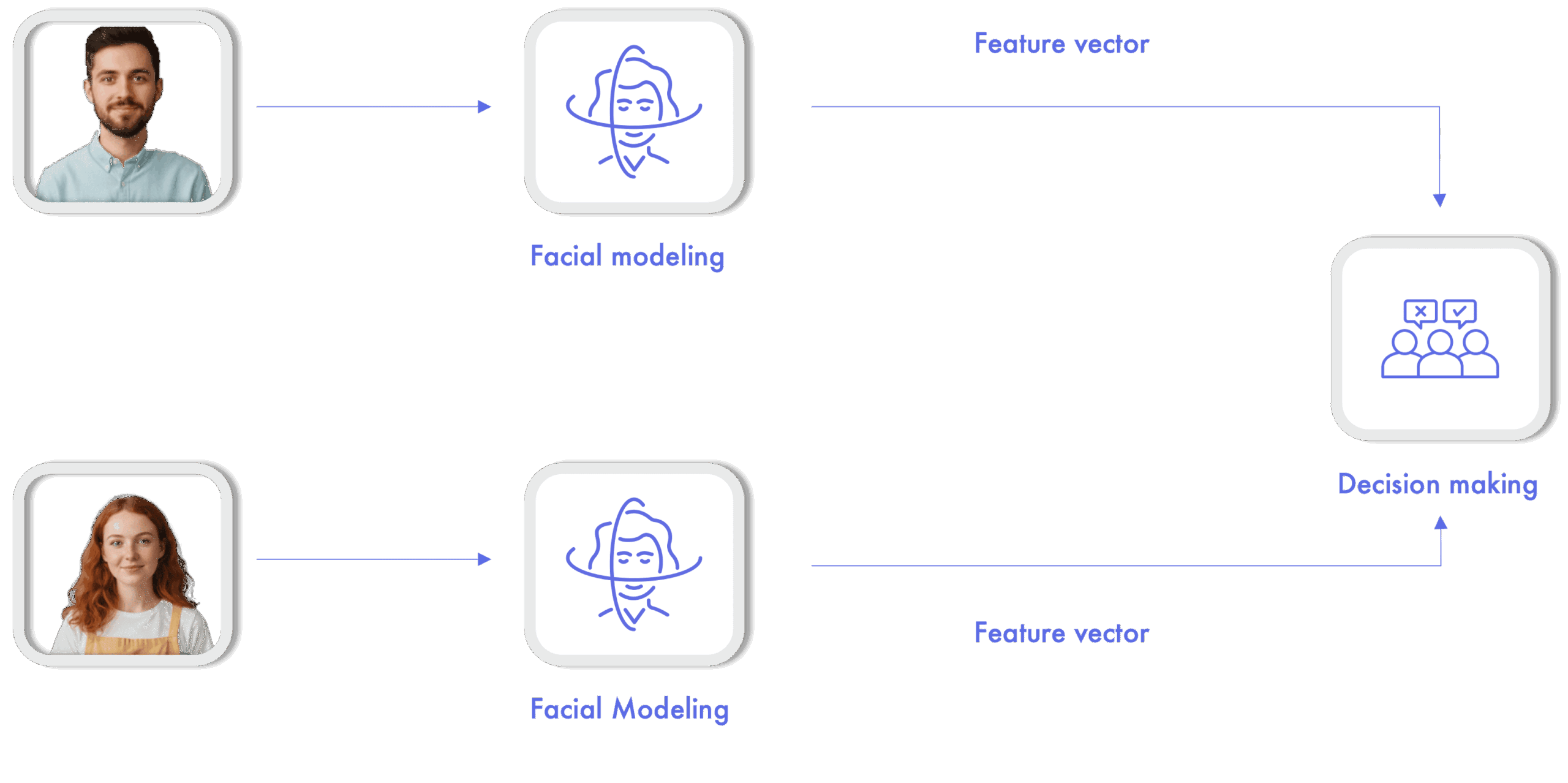
5. Decision making
The normalised numerical value obtained at the output of the comparison block may not be very descriptive and therefore needs to be contextualised. The objective of the final decision making stage is to return an interpretable response from this numerical value.
This response can be a binary value (identity verified/unverified) or a label with the identity associated with the input user in the case of identification.
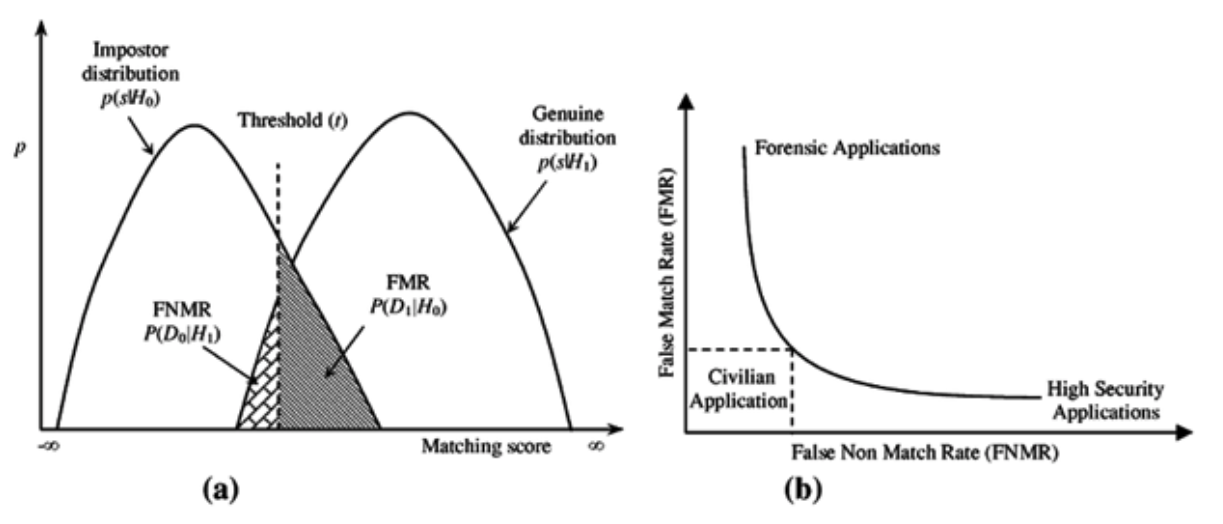
To make these decisions it is necessary to establish decision thresholds on the numerical values of the comparison in order to achieve a balance between security (very strict thresholds, a very high degree of confidence in the resemblance is needed) and usability (more relaxed thresholds, a lower degree of confidence is needed).
Decision thresholds need to be adapted to the needs of each project by assessing the cost of a higher incidence of misclassification errors:
- False positive: incorrect verification of a person’s identity. This is a mistake that has a high cost in security applications, where letting an impostor through is a serious threat.

- False negative: incorrect rejection of a person’s identity. This is an error that has a high cost in forensic applications, where wrongly rejecting a person’s identity can be a serious problem.

Guide to face recognition
Download the complete guide of facial recognition in PDF
Use of face recognition technology
A biometric system based on face recognition has multiple applications where it is required to verify the identity of users in digital environments. These are some of the most interesting and widely adopted by the industry:
Digital onboarding
Remote customer registration processes require reliable verification of a person’s identity. For this purpose, facial recognition provides a useful tool not only to verify identity but also to ensure that there is no fraud, such as synthetic identity theft. Two examples of the integration of a digital onboarding system with facial recognition in the financial sector are Banco Continental’s Digital Account and Banco Agrícola Cuenta Fácil.
Access to digital operations
During the digital onboarding process it is possible to securely store the user’s biometric traits so that this information can later be used to control access to different operations securely: digital payments, access to transport, collection of prizes in online gaming, etc.
ATMs
In recent months, many ATMs have been incorporating digital cameras that allow the biometric identity verification process to be performed in a simple way. This brings agility to transactions, as well as adding an extra layer of security by preventing the possible criminal use of bank cards (either by replacing the traditional PIN code or by providing two-factor authentication).
Time and attendance control
New regulations regarding time and attendance control open the door to massive use of biometrics as an agile method of registering or clocking in during the working day, while preventing fraudulent practices.
It is possible to digitalise the customer registration process in hotel establishments, obtaining all the necessary information that can also be used to manage access to rooms by means of biometric verification subsequently.
Education
Universities and other educational institutions can make digital identity verification available to students during the enrolment process. Furthermore, biometric authentication allows for an accurate record of attendance, facilitating the assessment of progress and compliance with training requirements.
Event management
Facial recognition can facilitate access to events with large crowds, such as concerts, festivals or conferences. Attendees can register and then enter the event using biometrics, simplifying the entry process and improving security by preventing unauthorised access.
Implementing this technology eliminates the need to present physical documents and streamlines the flow at counter check-in.
Identity validation in delivery and logistics
Facial recognition can be used to verify the identity of parcel recipients. It ensures that goods are delivered securely and to the right person.
Facial recognition in social media
Biometric technology can facilitate users’ access to their profiles and, at the same time, boost account protection and help age verification to prevent access by children.
Facial recognition and society
The possibility of carrying out identity verification using biometric methods offers great advantages, but like any other technology based on human-machine interaction, it involves some challenges when we analyse its social implications.
Given that this type of tool can be used in many different contexts (some of them critical), it seems necessary to reflect on the most relevant aspects involved in its use, including the advantages and challenges related mainly to the field of security.)
Authentication beyond passwords
Historically, passwords have been the most widely used authentication method to verify people’s identity in digital environments. We are all forced to remember different sequences of characters that prove that we are authorised to carry out different operations: bank account management, access to email, access to private environments, etc. This requires us to use passwords that, in order to be secure, must be complex and frequently updated.
Indeed, this is its weakest point. For convenience reasons, it is common to use the same password for different services or to use a simple and easy to remember password, increasing the possibility of being hacked and used for fraudulent purposes.
Through its application in identity verification systems, biometrics simplifies and strengthens the process, moving from something we know (the password) to something we are (our biometric features). The integration of facial recognition systems in business solutions brings interesting benefits in three main areas:
- Agility: it is possible to automate the entire process (from capture to decision making), saving time in operations and improving the user experience by avoiding complex passwords.
- Security: biometric technologies have proven to be a robust method for determining a person’s identity with guarantees. Furthermore, we remove the threat of password theft.
- Modularity: the technology can be easily integrated into existing applications and can be used in conjunction with classic password-based methods to implement two-factor authentication systems.
Inclusive biometrics
Inclusion in facial recognition is measured not only in terms of technological accuracy, but also in the ability to reach everyone, regardless of where they live or what resources they have. In many areas, particularly in rural zones or regions with limited infrastructure, access to digital services remains a challenge.
Inclusive biometrics seeks to bridge this gap by offering solutions that do not require the latest devices or high-speed connections to function properly. In this way, a person living in a remote community can identify themselves and access financial, healthcare, or administrative services in the same way as someone in an urban environment.
The ultimate goal is for facial recognition to become a universal gateway to digital identity, rather than a factor that increases inequality between those with greater and lesser technological resources.
Humanitarian biometrics
Facial recognition also plays a crucial role in contexts where digital identity can mean the difference between receiving aid or being left behind. In humanitarian crises, refugee camps, or areas without solid infrastructure, biometrics make it possible to provide basic services to people without official documentation.
By linking a biometric identity to the delivery of resources or social programmes, international organisations can manage aid more efficiently and securely, reducing fraud and ensuring that assistance reaches those who truly need it. In this sense, biometrics is not only a technological tool but also an instrument of dignity and protection.

Face recognition security challenges
Secure and reliable systems
Security (understood from a general point of view) is a key element in biometric recognition systems. Both the reliability of the results and the trust involved in the process depend on it. In order to successfully implement a biometric system in a commercial solution, security threats must be minimised.
Therefore, the analysis carried out in ISO/IEC 30107-1 regarding the main potential attack points in a generic biometric system is very useful for this purpose.
Although the threats may seem too many, it is possible to group them into three blocks according to their nature:
- Presentation attack: this is an attack to the biometric capture device with the aim of interfering with the correct functioning of the system. Its detection is crucial in a biometric solution and will be discussed in more detail in the following section.
- Attacks on processes: each of the functional blocks is susceptible to attack with the aim of modifying its operation. Examples of such actions could be the replacement of the model used for feature extraction (rare) or the modification of decision thresholds to interfere with the system and make it more permissive.
- Attacks on communication channels: any connection point between blocks can be intercepted either to modify the information being transmitted or to inject different information. A clear example could be the substitution of the feature vector of the comparison image to obtain different results or the modification of the numerical value of the comparison to interfere in the final decision.
Injection attacks, which once seemed distant, are now commonplace. They essentially involve inserting biometric data into a system to impersonate another individual, deceiving the system and gaining unauthorised access.
At this point it is interesting to mention data protection, the raw material of the biometric system. The information used in a facial recognition process is considered as a special category by the General Data Protection Regulation (GDPR) and therefore subject to the highest protection given its personal nature.
It is therefore necessary to work with the utmost care in information security policies, ensuring that even in the case of a data leak, it will not be possible to recognise individuals in a biometric database by reconstructing the original features (facial image) through reverse engineering.
In this regard, facial modelling algorithms based on deep learning provide great robustness, as it is difficult to recompose the original image from the one generated by the feature vector (hence they are also known as unidirectional).
The combination of this type of algorithm together with the encryption of all the information generated, enables the implementation of secure systems that meet today’s strict regulations.
The threat of identity theft
The most common type of attack that a biometric system can face is the presentation attack: a user acting on the capture module with the intention of spoofing another person or concealing his or her own identity. In most cases, the purpose of the attacker is to supplant another person’s identity without authorization, which is why it is common to replace the general term “presentation attack” with the more specific term “spoofing attack”.
The capture subsystem is the most vulnerable element as it is the most exposed. For this reason, it is necessary to focus all efforts on detecting all suspicious actions. An important concept with regard to spoofing attacks is the attack instrument (i.e. the biometric feature or object used to carry out the attack).
In the field of facial biometrics, it is common to use attack tools such as masks, images or recordings showing the face of the person to be impersonated. The objective of an automatic spoofing attack detection system will therefore be to analyse the input information to detect traces of the use of such tools.
This process is by no means trivial and represents a huge challenge, especially when it comes to generalising the operation of attack detection algorithms to the real environment, where we will encounter a wide variety of situations that are sometimes difficult to control.
Deepfakes detection
Deepfakes are audiovisual manipulations that use deep learning techniques to create fake content, often to impersonate a person in a video. This manipulation presents a significant challenge in detecting impersonation attacks, as they can potentially fool facial recognition systems.
It is essential to analyse multiple aspects of the multimedia content to identify deepfakes. It includes assessing visual and temporal inconsistencies, such as anomalies in facial appearance or unnatural movements. Checking for consistency with the context and environment in which the video is supposed to have been recorded is also crucial. Furthermore, comparing biometric features can provide valuable clues about the authenticity of the content.
Some of the measures implemented by spoofing attack detection systems can be grouped into two blocks according to the need for interaction with the user:

Collaborative measures
These measures require the active collaboration of the user and are focused on detecting there is a real person (liveness detection). This involves analysing behaviours or voluntary responses to small challenges in order to determine whether the person carrying out the analysis is present at the time of the analysis. In the case of facial recognition, it is common to ask the subject to make a gesture such as a smile or a side-to-side head movement.

Non-collaborative measures
Non-collaborative measures are those in which the active collaboration of the user is not required (passive liveness detection). They can be based on the analysis of involuntary responses (such as the measurement of pupil contraction to a light stimulus) or on the analysis of the scene through the evaluation of environmental conditions: analysis of textures to detect the use of screens, detection of suspicious elements…
Renewable Biometric References (RBRs)
Protecting biometric templates is essential for maintaining trust in any facial recognition system. Renewable Biometric References (RBRs) represent an evolution in the way sensitive information is managed: they make it possible to revoke, replace, or update a facial template if it is suspected to have been compromised much like changing a password.
This is achieved by applying mathematical transformations to the original biometric data, generating unique and irreversible representations that do not allow the face to be reconstructed or linked across different systems. Thus, even if a database were compromised, RBRs would prevent that information from being reused or correlated. This approach gives biometric systems an additional layer of security and privacy, fully aligned with data protection principles.
Homomorphic encryption
This cryptographic technique complements RBRs by providing additional protection when data are being processed. Homomorphic encryption allows comparisons and verifications to be performed on encrypted information without the need to decrypt it at any point.
In a facial recognition system, this means that both the stored template and the captured data can remain encrypted throughout the entire process. The result is end-to-end privacy, which reduces the risk of exposure even in distributed or cloud-based environments.
This type of encryption stands out as a strategic tool for ensuring confidentiality in the processing of biometric data, as well as for enhancing security and regulatory compliance.
Privacy by design
The Privacy by design principle establishes that data protection must be an integral part of a system’s design and architecture, rather than being added later as an extra control once development is complete. Its purpose is to ensure that privacy is embedded from the outset, becoming an essential element in the very DNA of any facial recognition solution.
Applying this approach involves minimising the amount of information collected, incorporating anonymisation or pseudonymisation techniques, ensuring transparency in the processing of biometric data, and giving users genuine control over their digital identity.
In the final process it is necessary to combine the information from both measures to return a result about the probability of attack. Then this is combined with the result of the matching between the document image and the one extracted from the capture device to make a final decision about the whole identity verification process, providing confidence about the process.
Face recognition: Ethics, bias and accessibility
When analysing the social implications of the use of face recognition technologies, the ethical factor is crucial. As with any disruptive technology, there are great opportunities for process improvement, but there are also risks that self-interested use could have negative effects.
There is latent concern about the use of face recognition systems that could lead to excessive social control by some governments (as in the case of China and its citizen’s points-based ID card), as well as the not always transparent use of facial biometric algorithms by private companies with the aim of obtaining the maximum information from their users.
In this sense, there is a need for clear regulation regarding the permitted uses and limitations in terms of personal data protection policies, which are already being implemented in many Western countries.
Biometric operations in the privacy and data protection framework
When we talk about the processing and treatment of biometric data, it is vital to consider the technique used, the specific nature of the processing, its scope and, most importantly, the objectives pursued because biometric operations can have different impacts on privacy and affect individuals differently.
Biometric data processing techniques are based on capturing and analysing physical features, making identifying individuals possible.
Each biometric technique must be assessed attending the principle of necessity, appropriateness and proportionality, its purpose, and its impact on individual rights.
It is important to note that according to the General Data Protection Regulation (GDPR), the user’s explicit consent is required, and an impact assessment of the system must be performed.
Demographic bias and facial recognition
Another aspect of great social relevance is the need to develop biometric systems that are accessible, inclusive, and fair. Machine learning algorithms are trained on thousands of examples from databases, meaning their performance depends directly on the quality, diversity, and representativeness of those data. Various studies have shown that, in the case of facial recognition systems, performance is not always uniform across all users, revealing the presence of demographic biases. Variables such as gender, age, or ethnic group can influence recognition accuracy when certain communities are underrepresented in the training data.
As a result, the system may exhibit unequal behaviour depending on people’s sociodemographic characteristics. To minimise these biases and promote technological fairness, we work on creating datasets that are balanced in sociodemographic terms and apply algorithmic fairness strategies during model training. In this way, we aim to ensure consistent and fair performance across all population groups, while also guaranteeing truly universal access to our biometric systems.
A look into the future of face recognition technology
In a constantly evolving industry such as biometrics, it is difficult to make long-term forecasts, but it is true that there are certain consolidated trends in the sector that allow us to foresee what major trends will emerge in the near future.
The artificial intelligence dialectic
Artificial Intelligence is undoubtedly one of the main enabling technologies that within the industry 4.0 paradigm allow further development of the processes and services offered by technology companies. However, this growing presence also implies a growing risk of non-legitimate use, as these technologies can be used to create sophisticated attacks that are increasingly difficult to detect.
In the field of facial recognition, there is evidence of the use of artificial intelligence techniques to generate artificial biometric features (commonly known as deep fakes) or even to try to regenerate the original trait from the feature vector. This struggle between stakeholders forces vendors to stay one step ahead of attackers by implementing working methods based on continuous improvement to maintain the reliability of systems.
Regulation with a special focus on European AI legislation
As artificial intelligence becomes increasingly integrated into various processes and services, the European Union has introduced regulations to ensure responsible, ethical, and secure development. Among these regulations, the AI Act stands out, along with other directives covering areas as diverse as payment services, anti-money laundering measures, and customer identification. Together, these regulations form the framework guiding the implementation of biometric technologies.
Reference to the AI Act and new regulations approved by the European Commission (February 2025)
In February 2025, the European Commission approved new regulations reinforcing the AI Act, aimed at promoting the safe and ethical implementation of artificial intelligence in critical applications. This update provides more specific guidelines for integrating AI technologies into biometric verification systems, establishing strict requirements to protect citizens’ fundamental rights.
Among the most significant aspects is the obligation to ensure that the technologies used comply with criteria of transparency, traceability, and risk minimisation. This strengthens the regulatory framework, preventing the misuse of AI while fostering trust in digital solutions.
Compliance of Mobbeel’s facial recognition with European AI regulations
The facial biometric technology implemented aligns with the guidelines established in the European Artificial Intelligence regulatory framework, ensuring compliance with current regulations and confirming that it is not among the prohibited systems listed in Article 5 of Regulation (EU) 2024/1689.
Operating under a 1:1 model, this system only compares the captured image with the user’s pre-registered reference, integrating advanced facial detection functions, image quality analysis, biometric vector extraction, and presentation attack prevention.
Additionally, its risk classification is considered low, as its use is entirely voluntary and based on the subject’s explicit consent.
Other relevant regulations
PSD3
Alongside these developments, regulations are being introduced to oversee the digital activities of key industries, such as banking, aiming to curb potential abuses like money laundering and tax evasion. A key example is the revision of the regulatory framework for payment services through the proposed third Payment Services Directive (PSD3), complemented by a regulation (PSR). The main objectives of this regulatory package are:
- Strengthening security in electronic transactions by increasing authentication measures and fraud prevention strategies, including tackling new types of fraud such as spoofing.
- Enhancing consumer protection by ensuring greater clarity in account statements, precise details on fees, and expanded user rights, particularly in cases where funds are temporarily withheld.
- Promoting competition by allowing non-bank payment service providers to compete on equal terms with traditional banks, while optimising the functioning of open banking.
It is important to note that PSD3 is not yet in force. The European Commission presented its draft in June 2023, and the proposal is currently under review and debate. It is estimated that, once formally adopted and transposed into the legislation of each member state—along with an adaptation period for businesses—PSD3 could start being implemented between 2026 and 2028.
AML
In a similar vein to the changes introduced in early 2020 with the adoption of the AML5 directive, the AML6 directive aims to further tighten control measures in the fight against money laundering. This new directive requires companies across various sectors to adopt enhanced due diligence protocols, ensuring not only the accurate identification of all parties involved in each transaction but also expanding the definition of fraudulent activities by incorporating new offences and emerging risks.
In this way, AML6 contributes to improving the early detection of suspicious transactions, strengthening transparency throughout the value chain, facilitating the identification of ultimate beneficiaries, and enabling a more effective response to illicit activities.
KYC
Within the implementation process of AML solutions, KYC (Know Your Customer) plays a key role. The purpose of KYC is to gather all necessary customer information at the point of service onboarding, ensuring the user’s identity is reliably verified.
Identity verification is therefore a key component of this process, where facial recognition technology can offer significant advantages.
Additionally, the guidelines provided by the European Banking Authority (EBA) and compliance with SEPBLAC regulations offer essential directives for the consistent implementation of biometric technologies within the financial sector.
Sustainable facial recognition
The future of biometrics depends on being sustainable, both from an environmental perspective and from a technological one. Facial recognition systems require processing and storage infrastructures that, if poorly designed, can lead to high energy consumption.
Sustainability involves optimising algorithms to make them more efficient, adopting cyber-resilience practices that extend the lifecycle of solutions, and investing in infrastructures that are environmentally responsible. At the same time, it also means designing business models that respect users’ privacy, avoiding the misuse of data and aligning with ethical principles.
Mobbeel face recognition solutions
Since our foundation in 2009, Mobbeel has developed products for identity verification. We were pioneers in applying biometric recognition technologies to mobile environments using only the standard sensors of a mobile device.
A large number of top-tier clients in different sectors, such as banking and finance, insurance, health, telecommunications and online gaming, rely on our technology to validate their clients’ identity in a variety of scenarios.
From the first moment that they begin their relationship through identity verification in a digital onboarding process, the multi-biometric recognition each time they access the system or authorise a transaction, to the biometric signature to validate legal contracts or agreements.
Face recognition functionality is included as a core element in two of our products:
- MobbScan: our digital onboarding solution that complies with KYC and AML regulations. It allows the extraction and validation of personal information obtained through the analysis of identity documents as well as secure identity verification through facial recognition. MobbScan is flexible and modular, and can be adapted to the needs of each specific project. It currently supports more than 250 different documents (ID cards, driving licences, passports) from 194 countries, with the possibility of easily adding new document types.
- MobbID: a multi-biometric identity verification solution that allows validation of the identity of customers through the analysis of one or several biometric features such as face, iris, fingerprint, voice or biometric signature, thus integrating identity fraud controls. The process can be carried out both online and offline, allowing it to be used even in low connectivity conditions. Like MobbScan, MobbID also allows a flexible and modular implementation.
Complete KYC process where the identity of the ID card holder is verified with facial recognition: MobbScan
NIST’s role in facial recognition assessment
The National Institute of Standards and Technology (NIST) is the US Department of Commerce agency charged with promoting innovation and industrial competitiveness by setting standards and quality measures.
In facial recognition technology, NIST plays a crucial role in providing impartial and rigorous assessments of facial recognition systems, which contributes to improving and standardising this technology.
Its testing and analysis help the industry to develop more accurate and secure systems while providing users and regulators with valuable information on the performance of these solutions.
Performance assessment of Mobbeel’s biometric algorithms
The assessments of this body involve vast testing of facial recognition systems provided by a wide range of technology providers, including Mobbeel.
Facial recognition algorithms are evaluated for different purposes, including analysing the quality of these algorithms and ranking them according to their accuracy and efficiency in different scenarios.
These assessments involve rigorous testing in different scenarios, ranging from ideal conditions to challenges with low lighting and variations in facial expression, among others.
1:1
NIST has assessed Mobbeel’s 1:1 facial verification technology.
In Mobbeel’s latest evaluation in October 2024, our algorithms configured in VISABORDER (which compares the identity document image with similar selfies for digital onboarding processes) achieved the following performance indicators:
- FNMR = 0.0045
- FMR = 0.000001
Explanation of NIST values
It is worth noting that, at the defined operating point, the false negative rate is 0.0045, corresponding to a false positive rate of 0.000001.
These results indicate that if we configure the technology with a security level that limits false positives to just 1 in 1,000,000 attempts, meaning that only in one instance would an unauthorised user bypass the system, then 45 legitimate users per 10,000 attempts would be rejected and would need to repeat the process.
It is necessary to mention that the assessments performed by NIST are not limited only to face matching 1:1. They also extend to face identification 1:N, which is the process of identification where seeking an identity among a set of people, such as in face databases.
1:N
Our technology has received a positive evaluation by NIST in the 1:N category. This distinction means that our solution has been validated to perform face identification operations on sets of previously registered identities.
This capability is essential in versatile projects that demand the identification of individuals within a larger database, giving our users the confidence and security needed to perform face identification operations effectively and accurately.
Download the face recognition guide as a PDF document
Download our guide to facial recognition and learn more about the origins of the technology, current techniques, use and future developments.

What will you discover in the face recognition guide?
- Learn about the history of facial recognition. Origins and evolution.
- Learn how facial recognition systems work.
- See the different uses and applications.
- Understand the different implications of the technology in our society today.
- Discover the challenges in cybersecurity.
- Learn about the regulations involved in biometric processes.




