We are moving towards a unified digital market where the future of digital identity plays a critical role in building trust and securing remote services. So central has it become that digital identity is now a strategic domain — and a global battleground.
On the geopolitical stage, opposing models are clashing: centralised systems controlled by a single authority — like India’s Aadhaar — versus decentralised architectures such as Self-Sovereign Identity (SSI), where individuals maintain control over their own data.
This divide is also reflected in who governs identity: some states push for national, biometric identity schemes, while tech companies champion digital wallets and private verification platforms.
These contrasting approaches will shape who holds the power to manage digital trust and personal data in the years ahead. The way we handle digital identity today will define access to fundamental rights and vital services for millions tomorrow.
Global perspectives on digital identity: Europe, the United States and China
How is digital identity evolving across different regions of the world?
In Europe, the dominant approach is one of coordinated regulation across Member States. Under the eIDAS/EUDI framework, each country must provide a national digital wallet where citizens can store official credentials that are recognised EU-wide — and issued by a central authority. The vision is to ensure interoperability, user control and privacy by design, enabling seamless access to cross-border public and private services.
The United States, by contrast, lacks a unified federal system like the one being developed in Europe. The American approach leans heavily on private-sector innovation. Various tech consortia have pushed forward digital driving licences (mDLs), while major players like Apple and Google now allow official ID documents to be integrated into their respective iOS and Android wallets. Meanwhile, both Democrat and Republican administrations have prioritised combating identity theft, reflecting a bipartisan consensus on the need for stronger protections amid rising cyber threats.
In China, the model is markedly different — a centralised state-driven system with a strong emphasis on surveillance and control. The government has proposed an “Internet ID” initiative that mandates online registration using the national ID card and facial recognition. This system gives the state wide-reaching access to individuals’ digital activity, aligning with broader goals of social monitoring and digital governance.
Digita ldentity in Europe
Focusing on the European Union, a clear regulatory roadmap is already in place for the coming years. The eIDAS 2.0 Regulation (also referred to as EUDI – European Digital Identity), published in April 2024 as an update to the original 2014 eIDAS Regulation, lays out a common framework for electronic identity across the EU. Under this new regulation, each Member State must issue digital identity wallets by 2026, enabling both citizens and businesses to identify themselves securely in interactions with public and private sector organisations.

These electronic wallets aim to provide a “secure, trusted and privacy-preserving” identification system for all Europeans, in line with the vision outlined by the European Commission. At the same time, and alongside these initiatives, interest continues to grow in decentralised models (SSI) and the adoption of technologies like AI and blockchain for managing digital identities.
Digital identity wallets
A Digital Identity Wallet is an app—either mobile or cloud-based—that stores, manages, and presents a person’s digital credentials, essentially replacing the traditional leather wallet used for holding cash, ID cards, and other documents.
The European Data Protection Supervisor (EDPS) defines a Digital Identity Wallet (DIW) as: “an application that allows for the secure storage, management, and sharing of personal identification data.”
Just like a driving licence or a credit card, the user carries their credentials on their mobile phone. It’s not uncommon to see studies drawing parallels between a digital wallet and its physical counterpart, since this digital wallet is stored on the user’s device and contains various credentials such as an employee ID or a driver’s licence—much like a traditional wallet kept in your pocket or handbag.
These digital wallets give users control over which personal attributes they share with third parties—such as their name, age, address, or professional certifications. Each credential (e.g. driving licence, university degree, medical certificate) must be cryptographically signed by a trusted issuing authority—either governmental or private—to ensure its authenticity.
In the traditional digital wallet model, “the trustworthiness of the attributes is guaranteed through the cryptographic signatures of authorities, typically via a certificate hierarchy.”
In practice, this means that a state or certified issuing authority provides each credential (like a digital passport), which is then stored in the wallet.
Under the eIDAS 2.0 regulation, these credentials must conform to international standards. For example, implementations are required to use the W3C Verifiable Credentials model to ensure both interoperability and privacy.
Given the need for secure and private communication, data is encrypted and only the strictly necessary attributes are shared. The European model stipulates that each Member State must provide at least one official wallet for its citizens and businesses. This wallet, under the EUDI (European Digital Identity) framework, will streamline tasks such as logging into government portals, signing electronic documents, or proving age without paperwork—all while keeping the user in full control.
Several European governments are already piloting national wallets, and consortia like the EUDI Wallet Consortium are exploring use cases. For instance, a citizen might store their driving licence and university diploma in the wallet and later present only the relevant information—such as “over 18” or “degree in Civil Engineering”—to an online service, without disclosing more than necessary. Likewise, companies could accept federated logins via the eIDAS wallet for streamlined digital onboarding (KYC) or secure payment processes.
Identity proofing in secure digital identity wallets
Just as crucial as the use of digital identity wallets is the ability to reliably verify the identity of the person using them. This is where Identity Proofing comes in—a process designed to authenticate a user’s identity before granting access to a system or service, commonly referred to as identity verification.
Typically, identity proofing involves a combination of methods, such as cross-checking personal data against external databases, analysing official identity documents, and confirming identity through facial recognition technology.
 Although identity proofing itself is not classified as a qualified trust service under the eIDAS regulation, it is nonetheless a vital component within the broader framework of such services. As a result, many Qualified Trust Service Providers (QTSPs) choose to outsource this function to specialised digital verification companies.
Although identity proofing itself is not classified as a qualified trust service under the eIDAS regulation, it is nonetheless a vital component within the broader framework of such services. As a result, many Qualified Trust Service Providers (QTSPs) choose to outsource this function to specialised digital verification companies.
-
To bring consistency and reliability to these procedures, technical standards were introduced in 2021 to ensure remote verification meets the same level of assurance as in-person checks. Key among these are:
-
ETSI TS 119 460 – This standard outlines the technologies and regulatory requirements for identity verification in trust services.
-
ETSI TS 119 461 – It sets out the security policies and standards that must be followed during identity proofing processes.
Together, these frameworks aim to align digital verification methods with stringent regulatory demands, enhancing both trust and usability in digital identity ecosystems.
-
Self-Sovereign Identity (SSI)
Self-Sovereign Identity (SSI) represents a fundamentally different approach to digital identity management—one in which individuals own and control their digital identifiers and credentials without relying on a central authority.
SSI is an identity management model that gives individuals full ownership and control over their digital identities, without relying on a central authority.
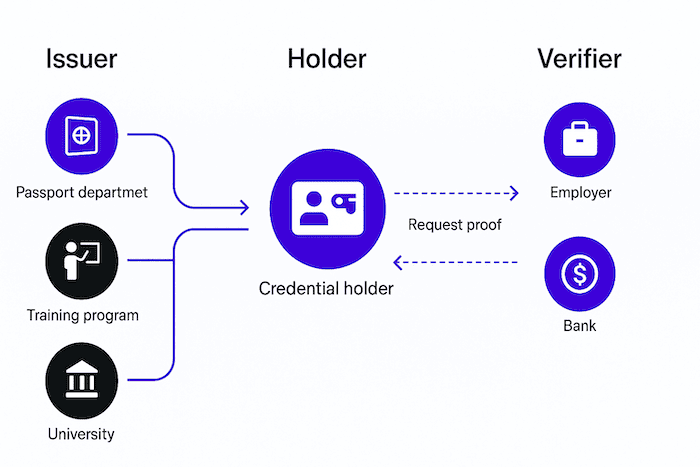
At its core, SSI empowers individuals to generate their own Decentralised Identifiers (DIDs) and receive Verifiable Credentials (VCs) from various issuers—be they public institutions or private organisations. For example, a university could issue a degree as a verifiable credential, which the individual then stores in their personal wallet and presents when needed—all without intermediary involvement.
Technically, the SSI model is grounded in emerging W3C standards:
-
Decentralised Identifiers (DIDs): A new kind of unique identifier that can be created by users themselves, linked to a DID Document stored on a blockchain or distributed ledger. This enables cryptographic proof of identity without centralised control.
-
Verifiable Credentials (VCs): A tamper-resistant data format used to express signed statements from an issuer (e.g. “Degree: Computer Science” or “Bank account verified”). These credentials allow for secure and extensible certification of information.
The potential of decentralised identity is vast, with a wide range of practical use cases. One prominent example is the European Blockchain Services Infrastructure (EBSI), which is building a cross-border digital identity framework using blockchain. In this model, users create and manage their own identities independently, without depending on centralised authorities—enabling seamless services across EU borders. In practice, this could simplify processes like recognising qualifications abroad or accessing public services in another country.
Other common use cases include:
-
Professional and academic credential verification: Candidates could store diplomas and work certifications in their wallets as verifiable credentials, allowing employers to instantly verify their authenticity during recruitment.
-
Health data sharing: Patients carry core medical records in their digital wallets and share them securely with doctors or hospitals—eliminating manual transcription.
-
KYC/AML onboarding: Banks and fintechs can reuse verifiable credentials (such as proof of identity or residency) issued by trusted providers, streamlining customer onboarding and compliance checks.
-
Cross-border government services: Migrants, for instance, could present verified records of employment or education from their home country, recognised by institutions abroad.
Ultimately, the vision behind decentralised identity is to foster a new ecosystem where any trusted entity—a university, a bank, a healthcare provider—can issue verifiable credentials, and individuals can manage them independently using DIDs and VCs. This model promises a more private, interoperable, and user-centric future for digital identity.
Key Differences: Identity Wallets vs Decentralized Digital Identity
Although both models use digital credentials in wallets, there are structural and governance differences:
| Aspect | Digital Identity Wallet (DIW) | Self-Sovereign Identity (SSI) |
|---|---|---|
| Nature | Tool (app, software) | Identity model/paradigm |
| Data control | User decides what to share | User owns and manages his entire identity |
| Issuance of credentials | Centralized authorities (governments, banks) | May include decentralized or alternative issuers |
| Verification | Requires connection to issuing entity in many cases | Self-sufficient cryptographic proofs |
| Infraestructure | Cloud or infra centralized | Decentralized networks (blockchain, DLT) |
| Privacy and Traceability | Depends on how it is designed | Máxima privacidad (zero-knowledge, selective disclosure) |
| EU example | EU Digital Identity Wallet | ESSIF (European Self-Sovereign Identity Framework) |
Regulatory framework in Europe: eIDAS 2.0, GDPR and AI Act
eIDAS 2.0 (EUDI Wallet Regulation)
The updated eIDAS 2.0 regulation governs the implementation of digital identity wallets across the EU. It mandates that each Member State must offer at least one official digital wallet for citizens and businesses, conforming to common technical standards. These wallets are expected to support a range of qualified trust services, such as qualified electronic signatures, which can be integrated into the wallet architecture.
A key principle of eIDAS 2.0 is GDPR compliance by design: wallets must ensure that users retain full control over their personal data. This means stronger emphasis on explicit consent, data minimisation, and user-centric governance throughout all digital identity processes.
GDPR (General Data Protection Regulation)
The GDPR remains fully applicable to all digital identity systems in Europe. It places strict limitations on how biometric data—such as facial features or fingerprints—is used. Since these qualify as special category data when used for identification, their processing requires:
- Explicit consent, or
- Another valid legal basis under Article 9 of the GDPR.
Any organisation handling such data must also implement robust safeguards, including transparency, data protection impact assessments, and appropriate security measures.
AI Act (EU Artificial Intelligence Act)
As the world’s first comprehensive AI law, the AI Act introduces strict controls over AI-powered identity systems. It distinguishes between acceptable and prohibited uses, especially around biometric identification:
- Real-time remote biometric identification (e.g. facial recognition via CCTV by law enforcement) is prohibited, except under tightly defined exceptions (e.g. imminent threats, serious crime).
- Non-real-time or remote biometric verification (e.g. identity proofing via facial recognition during onboarding) is classified as high-risk. This triggers strict obligations including:
- Risk assessments
- Human oversight
- Transparent database logging
- The AI Act prohibits biometric categorisation based on sensitive traits like race, religion, or sexual orientation—deeming such use cases ethically and legally unacceptable.
Together, eIDAS 2.0, GDPR, and the AI Act establish a regulatory triad that aims to enable secure and privacy-preserving digital identity systems across the EU. They strike a balance between technological innovation and the protection of fundamental rights.

Key challenges
- Deepfakes and advanced impersonation: the rise of generative AI has made it possible to create highly convincing synthetic images, videos, and voice recordings. Today, it’s virtually impossible to tell a deepfake from the real thing with the naked eye. This poses a serious challenge to traditional biometric verification systems, as it becomes increasingly feasible to clone a legitimate user’s face or voice. To defend against such threats, additional layers of security—such as liveness detection—are essential. Technologies like those developed by Mobbeel provide these safeguards, verifying that there is a real, live person in front of the camera. Without such measures, attackers could fool identity systems using pre-recorded videos or 3D masks.
- Spoofing attacks (phishing and identity fraud): attackers are leveraging AI to carry out increasingly sophisticated identity fraud and phishing attacks. For instance, they can use injection attacks—employing virtual cameras to feed synthetic footage into identification systems—or create forged identity documents from genuine user data. AI tools now make it easy to generate highly realistic fake documents and automate credential theft. This raises the bar for fraud, including voice spoofing in call centres and the creation of entirely fake digital identities. At Mobbeel, we’ve tested documents generated by AI chatbots and our technology successfully flagged them as fraudulent.
- Traceability and privacy: paradoxically, one of the core strengths of decentralised identity systems—their emphasis on user privacy—makes fraud detection and traceability more complex. These systems are often designed so that data cannot be linked or traced back to an individual, which makes it difficult to track down malicious actors. A single credential may be reused anonymously, and if it’s abused, there’s no central registry to consult or audit. Additionally, once information is recorded on a blockchain, it cannot be deleted—creating tension with the “right to be forgotten” under European data protection laws. Striking a balance between effective traceability and preserving user privacy remains a major challenge.
Uso of AI in digital identity
As you’ve probably gathered, AI plays a dual role in this domain: it’s both a powerful tool for authentication and a weapon increasingly exploited by attackers with malicious intent.
Facial recognition powered by neural networks—particularly deep learning models like those developed by Mobbeel—is becoming more accurate by the day. A digital identity wallet can use facial recognition to compare a live image from a camera with official identity data. Given that “it’s now impossible to reliably distinguish” a real image from a synthetic one with the human eye, AI-backed biometric solutions have become “the only trustworthy defence” against deepfakes. These systems use convolutional neural networks trained on millions of facial images, capable of spotting subtle inconsistencies. They also incorporate liveness detection to ensure the user is physically present and genuinely engaging with the process.
When it comes to detecting forged identity documents, advanced OCR systems can scan and extract data from ID cards and passports, cross-referencing the photo with biometric data. Fraud detection modules use AI to examine the document’s security features—such as microtext, UV patterns, and background designs—for signs of tampering.
AI is also being used to tackle “voice deepfakes.” At Mobbeel, we recommend a multi-layered approach combining facial biometrics, liveness detection, and generative AI models to detect impersonation attacks—whether during document capture or in remote video calls.
Future scenarios: the convergence of digital wallets and decentralised identity
Looking ahead, the most likely scenario is the gradual convergence of both identity models—state-backed digital wallets and decentralised identity (SSI)—alongside increasing global interoperability.
Though often framed as distinct approaches, eIDAS wallets are expected to gradually integrate SSI features. For instance, discussions are already underway around adopting national decentralised identifiers (DIDs) that are interoperable across systems, and even linking them to public blockchains. Initiatives like EBSI (European Blockchain Services Infrastructure) already blend these models. Its “European Digital Identity” use case allows citizens to generate self-sovereign identities usable across public services in any EU country.
From the outset, the European initiative has prioritised cross-border usability, aiming to simplify identity verification processes between nations. In practice, this means a Spanish citizen could use their identity wallet in Finland without needing to adjust or reconfigure anything. Technical standards—ranging from usability guidelines to API protocols—ensure that credentials issued in one Member State are recognised across the entire EU. Globally, the widespread adoption of decentralised identifiers (DIDs) could extend these benefits beyond Europe.
What’s beyond question is the socio-economic impact of unified digital identities:
- For individuals, they promise convenience and privacy—removing repetitive paperwork and giving users more control over their personal data.
- For businesses and governments, they ease market expansion within the EU, reduce identity fraud, and enable innovative business models across sectors like fintech, regtech, and digital healthcare.
Recommendations for businesses: how to verify your users in the future
In light of this evolving landscape, companies and decision-makers should adopt a proactive stance. The first step is to assess existing identity systems in light of the requirements set out by eIDAS 2.0. Organisations must identify technological gaps and outline a roadmap for adopting compatible digital credentials.
Equally important is investing in cutting-edge technologies—particularly biometric authentication and AI-powered anti-fraud systems. These tools are not just an advantage; they are fast becoming a necessity.
Regulatory compliance will remain a top priority. Adhering to frameworks like GDPR and the EU AI Act means implementing strong privacy policies and conducting regular algorithm audits to detect and eliminate bias. At the same time, it’s vital to upskill both technical and legal teams in emerging concepts such as Self-Sovereign Identity (SSI), while also educating users on the advantages and risks of these new technologies.
And if all this feels overwhelming—don’t worry. Take a deep breath, count to ten, and then get in touch with us. With 16 years of experience in digital identity solutions, we know how to guide you through the wave of transformation that’s already upon us.
Get in touch with our team to discover how we use AI to fight AI—and prevent identity fraud through impersonation attacks.

I’m a Software Engineer with a passion for Marketing, Communication, and helping companies expand internationally—areas I’m currently focused on as CMO at Mobbeel. I’m a mix of many things, some good, some not so much… perfectly imperfect.

GUIDE
Identify your users through their face
In this analogue-digital duality, one of the processes that remains essential for ensuring security is identity verification through facial recognition. The face, being the mirror of the soul, provides a unique defence against fraud, adding reliability to the identification process.