The vast majority of identity documents in their most modern versions and electronic passports follow international standards and have NFC chips that stores and processes the document information without risk.
The information that the NFC chips incorporates usually varies and ranges from an electronic certificate and the keys for its use to the holder’s data in digital format, including the signature or the photograph printed in the document.
As many smartphones and tablets have sturdy cameras and NFC reader chips in their hardware this functionality can be used for digital onboarding processes in which the identity of a user is registered and verified through an identity document and facial biometrics.
There are multiple projects and use cases in which NFC technology of documents is used for identity verification processes in registries. Especially in those where security is critical.
Vueling and Aena use NFC reading technology to allow their passengers to enrol their biometrics remotely. These companies use NFC through their app and can go through the different controls through facial recognition when they are at Josep Tarradellas Barcelona-El Prat airport.
What is NFC technology and how does it work to read identity documents?
NFC (Near Field Communication) technology allows contactless, wireless and short-range communication (no more than 15cm) between two devices to make payments or exchange information.
To carry out the process of reading an identity document through NFC, the user must have a smartphone (Android or iOS) with a camera and NFC reading capacity. The steps of the process are:
1. Firstly, scan the MRZ (Machine Readable Zone) of the identity document using the device’s camera. In this area, there are three pieces of information (date of birth, issue date and document number). These pieces are essential to access the NFC chip and read the rest of the information.
2. Then, the user must bring the identity document close to the phone to read all its data via NFC (using the data read by OCR as the access key previously).

The extracted data includes a facial photograph of the holder in high resolution. If the reading of the document data is part of an enrolment or identity verification process (digital onboarding), we should add an extra step to that. The user is asked to take a life-sensing ‘selfie’ of their current face that will be biometrically compared to the one stored in the document.
What information does the NFC chip incorporate in Spanish identity documents?
Different types of ID coexist in Spain but only the last two versions have a chip that allows connection through NFC technology:
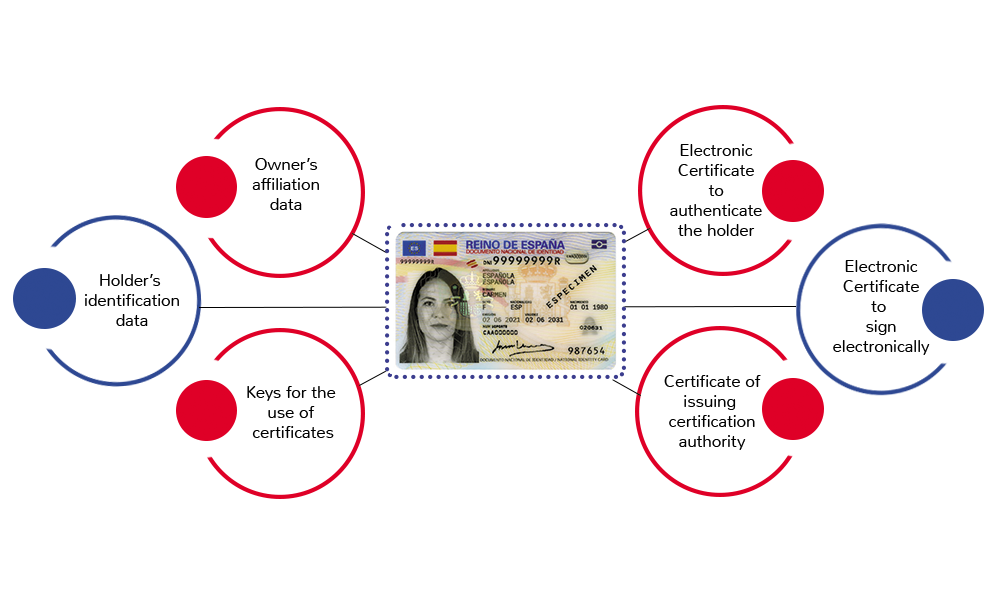
What data do the Spanish ID Card 3.0 and 4.0 chips include?
- An electronic certificate to authenticate the holder of the identity document.
- An electronic certificate that allows signing electronically (qualified signature).
- Certificate of issuing Certification Authority.
- Keys for the use of certificates.
- Identification data of the holder in digital format (high-resolution photograph, handwritten signature or fingerprint).
- Owner’s affiliation data
Security mechanisms in machine-readable travel documents MRTDs
The Spanish electronic passport and the ID Card in versions 3.0 and 4.0 have a contactless reader chip (NFC) that contains biographical information of the person (name, date of birth, nationality, etc.) and a face image.
To protect this data against different attacks, the documents implement a series of security measures defined in the ICAO International Standard, specifically 9303.
The different security controls that these chips implement try to ensure three things:
- Information privacy. In other words, the information cannot be read without the user’s consent, either by bringing an unauthorised reader closer to the document (skimming) or by intercepting the communication between the chip and an authorised reader (eavesdropping).
- Information authenticity. The information that has been read from the chip is authentic, issued by the competent authority of the issuing country, and has not been modified or altered.
- Chip authenticity. The information read is authentic and complete as well as the chip.
It corresponds to an original identity document and is not a copy.Spanish documents implement all three types of measures.
Information Privacy
The organisations that issue identity documents protect the information on the chips through cryptographic-based access control that prevents the following attacks:
Skimming or unauthorised reading by bringing a reader closer to the identity document. Although the reader would have to be quite close to the chip (a few centimetres) an attack is possible in certain situations. To prevent this kind of attack, the documents implement some type of access control in which a password is required to read the contents.
Eavesdropping on the communication between the chip and a reader. To prevent this type of attack, access control protocols exchange keys between the reader and the chip and encrypt the communication between both parties with these keys.
There are two information access control protocols:
- Basic Access Control (BAC). It is the simplest (based entirely on symmetric cryptography) and the oldest of the two protocols and is based on the fact that to read the contents of the chip it is necessary to know three pieces of information from which an access key is derived:
- Document number
- Date of birth
In MobbScan, our document scanning solution allows reading by NFC to avoid the inconvenience that the user has to enter this data manually. The reading is done automatically through the smartphone’s camera and OCR technology.
The authenticity of the information
Unlike the measures to protect privacy, which focus on controlling access to information, there is another set of measures whose goal is to ensure that the information read from the chip was issued by the competent authority and has not been modified or altered.
This set of measures is called Passive Authentication (PA) in the ICAO 9303 terminology and is based on the concept of digital signature, widely used in many fields:
- The data (name, document number, dates, photo and so forth) are signed by the issuer of the document (the country’s government) with a private key that remains secret in its custody.
- The recipient of this information can read the information on the chip, and its signature and check its validity using the public keys that governments publish. The signature will not be validated if the information has been altered.
In practice, everything is a little more complicated due to the variety of cryptographic algorithms implemented by the different issuing states, because there is not a single certificate but a “chain of trust” of certificates, and the difficulty of having a single standard source and trustworthy public keys of the different issuing states.
NFC chips authenticity
The previous measures provide access control to the information in the chip and prove that the information is authentic. In addition, they prove that it has been issued by the competent authority and has not been altered.
However, they do not prove that the information was read from the original document since the NFC chips could have been cloned (the equivalent of a photocopy in traditional documents).
Depending on the way in which it is used, this may be irrelevant or it may be absolutely necessary to prove that it is an original passport or ID and not a copy (and even that it is being presented by its legitimate owner, for which security measures come into play facial biometrics outside the scope of this document).
As anti-copy protection, the most widespread mechanism is the so-called Active Authentication.
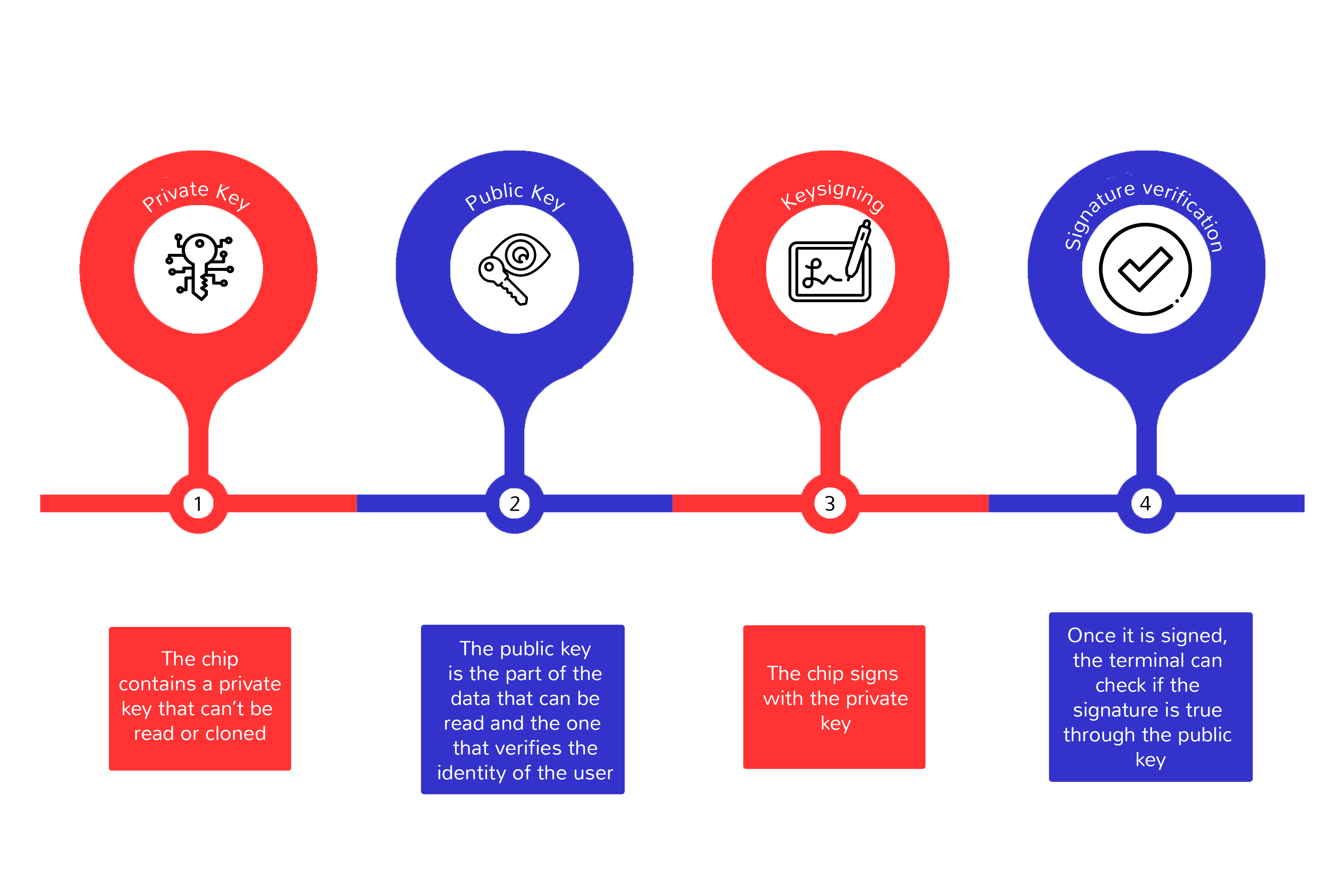
Active Authentication is again based on the principles of asymmetric cryptography together with the anti-tampering capabilities of the chips that are capable of offering a private zone that cannot be read or cloned. The operation is as follows:
- A private key resides in the private area of the chip that cannot be read or cloned (due to hardware capabilities).
- The corresponding public key is part of the chip data that can be read and has also been signed by the issuing country to verify its authenticity.
- The terminator chooses a random challenge and sends it to the chip for it to sign with the private key.
- When the chip returns the signed challenge, the terminal can use the public key found among the accessible data of the chip (and whose authenticity can be verified thanks to the signature of the country certificate) to verify that the challenging signature is correct.
Documents NFC reading with MobbScan
MobbScan, Mobbeel’s KYC solution, allows the information contained in certain identity documents that have NFC chips to be read by contact, complying with and implementing all the security mechanisms and controls of the chip, both those that refer to the privacy of the information, such as passive and active chip authentication.
In most cases, the enrolment flow can be done through OCR capture, since only a clear image of the document is needed. In that case, any identity document could be captured and any device with a camera could be used.
In cases where security is a critical requirement (airports), the level of security required against possible fraudulent documents cannot be only offered with the information provided by static images with light, in a totally unattended and remote process.
That is why MobbScan in NFC capture mode enhances the security of any onboarding process.
Success story: Aena, Vueling, and Mobbeel revolutionise passenger experience with biometrics and NFC
Over the past few years, the global landscape has highlighted the need for secure and contactless digital channels for airport procedures and processes. These public spaces have increasingly sought to optimise operations and enhance the passenger experience, from check-in to boarding.
In this context, Barcelona Airport introduced a pioneering European project driven by Aena and Vueling in partnership with Mobbeel as the technology provider. For the first time, all steps of the passenger’s customer journey were consolidated into a single process, including baggage check-in, eliminating the need to present identification documents at each stage.
With cutting-edge technology, passengers can register their facial biometrics and verify their identity by scanning their ID card or passport using NFC and taking a selfie as a liveness detection to ensure authenticity. This registration can also be done at physical kiosks at Barcelona-El Prat Josep Tarradellas Airport.
NFC technology enables short-range wireless communication between two devices. In this case, it occurs between the passenger’s mobile device, running Aena’s mobile application, and the NFC chip embedded in the ID card or passport.
When passengers wish to scan their ID card or passport, they simply bring their mobile phone close to the document. This physical action initiates NFC communication between the mobile device and the NFC chip on the document, ensuring secure and encrypted communication between the two devices. This feature is crucial to protect the privacy and security of the personal data included in the identity document.
During NFC communication, relevant ID card or passport data is extracted. It includes information such as the identification number, date of birth, and other necessary details for identity verification.
Once the identity document is verified, and after comparing the photo on a document with the selfie to establish an appropriate threshold for acceptance, passengers gain exclusive access to security checkpoints and the boarding gate, providing a faster and more secure travel experience.

I am a Computer Engineer who loves Marketing, Communication and companies’ internationalization, tasks I’m developing as CMO at Mobbeel. I am loads of things, some good, many bad… I’m perfectly imperfect.
SUCCESS STORY
Discover the pioneering aviation project where NFC is its essential piece.
This project integrates into a single process all the steps that passengers go through at the airport until boarding the plane, using biometric technology instead of showing their ID.