Biometrics has long since established itself as the most robust and user-friendly method of authentication, outperforming traditional approaches such as passwords or tokens. Today, technologies like face recognition and voice recognition are widely used across industries as varied as banking, telecommunications, public administration, and virtually any digital service where verifying an individual’s identity is essential.
That said, traditional biometrics comes with an inherent issue: while extremely difficult to reproduce, there is still a potential security risk linked to data leaks—the irreversibility of the original biometric data. Research has shown that, through highly complex reverse-engineering techniques, it may be possible to reconstruct original features from biometric vectors.
Although the effort required to recreate someone’s photo from a biometric template makes such attacks highly unlikely—especially since images of individuals can usually be obtained far more easily by other means—international data protection authorities often highlight this vulnerability when advising against the use of certain biometric systems.
Once a biometric template has been exposed, there is no mechanism to “cancel” or revoke that facial data within the system.
From a regulatory standpoint, under the General Data Protection Regulation (GDPR), biometric data is classified as a special category of information precisely because it cannot be revoked.
This creates a paradox: biometrics remains one of the strongest ways to authenticate identity, yet it can also introduce vulnerabilities if not properly managed. This is why a new generation of biometric systems and templates has emerged: Renewable Biometric References (RBRs), a term defined by the Spanish National Cryptologic Centre (CCN) in its CCN-TEC 013 guide Secure Biometric Technologies for Access Control. RBRs are also compliant with the ISO 24745 standard.
![]()
The international standard ISO 24745 on biometric information protection sets out three fundamental principles that any system must guarantee: irreversibility, unlinkability, and revocability of biometric references. However, most traditional implementations fail to comply with the principle of revocability—or cancellation.
A new generation of more secure templates
RBRs shift the paradigm by introducing a model in which biometric information is no longer stored as a fixed template or biometric vector in a database, but instead as a renewable, non-reversible mathematical representation that can be regenerated in the event of a security breach.
In particular, additional safeguards must be applied to biometric templates under the principles of Renewable Biometric References (RBRs), ensuring irreversibility, non-interoperability, and revocability.
This innovation enables biometrics to fully comply with the security and privacy principles set out by international standards and by the Spanish Data Protection Agency (AEPD).
What are Renewable Biometric References (RBRs)?
The ISO/IEC 24745 standard defines how biometric vectors or templates must be securely stored. According to this standard, biometric vectors should be:
-
Renewable
-
Revocable (cancellable)
-
Non-reversible
-
Non-interoperable
The main challenge lies in revocability. At present, if a vector is generated from the same photo using a neural network, the result will always be identical because biometric modelling is deterministic: the same input image always produces the same template. The principle of revocability seeks to ensure that a vector can be cancelled and replaced with a new, untraceable one if a database is compromised. This is precisely where RBRs come into play.
A Renewable Biometric Reference (RBR) is a mathematical representation of a biometric trait (such as a face, iris, or voice) designed to be irreversible, renewable, and diverse. In other words, it is a template derived from real biometric data that:
-
Does not allow reconstruction of the original biometric trait (mathematical irreversibility). RBRs are the result of a one-way transformation of the biometric vector. This means that even with full access to the reference, reconstructing the original trait is mathematically impossible.
-
Can be regenerated as many times as necessary without recapturing the original biometric data (revocability). Each template can be regenerated from the original biometric trait by applying new transformation parameters. This makes biometrics analogous to a password: it can be “changed” whenever a security compromise is suspected.
-
Can be generated differently for separate systems or applications (diversity and non-interoperability). This prevents identity cross-matching across databases.
![]()
To achieve this, a one-way transformation is applied to the feature vector using an irreversible, parameterised algorithm. The result is a mathematical object that prevents reconstruction of the original data.
This marks a clear break from the traditional model, where biometric data was stored as a static template and therefore exposed to the risk of reuse in the event of a breach.
Traditional biometric templates vs RBRs
In a conventional biometric system, the workflow is as follows:
-
The biometric trait is captured (e.g. a face).
-
Its main features are processed (minutiae, unique patterns).
-
A static biometric template is generated and stored in the database.
-
At each authentication, the system compares the new capture against the stored template.
The issue with this approach is that the template is a fixed representation of the original data. If an attacker gains access to it, they could, in theory, attempt to reconstruct the original biometric trait or reuse the same template across different systems (a cross-matching attack).
A Renewable Biometric Reference (RBR), by contrast, is essentially a biometric vector that has been secured through protection techniques, which may vary in type and approach:
-
It cannot be reversed to recover the original face, voice, or other trait.
-
It can be modified by applying new mathematical transformations, producing a “new version” of the template.
-
It can be customised for each service, preventing the same biometric identity from being tracked across multiple platforms.
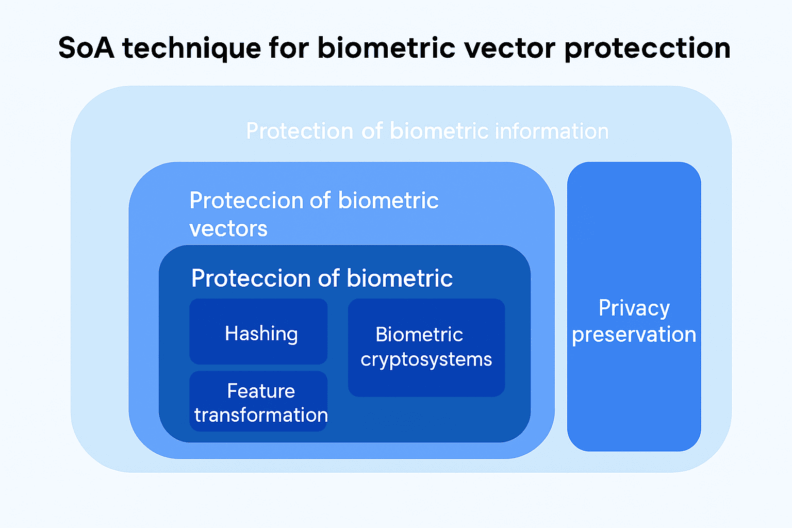
At Mobbeel, biometric information is safeguarded through homomorphic encryption for several reasons:
-
This technology ensures true end-to-end protection, as the original biometric data never needs to be decrypted at any stage of the process.
-
Matching takes place exclusively within the transformed (encrypted) domain, and only the final matching score is decrypted.
-
Encryption is performed using a specific context (cryptographic keys) that is securely stored in an external secrets manager.
-
To guarantee long-term robustness, the system uses algorithms that are candidates in the NIST post-quantum cryptography standardisation process, making it theoretically resistant even in a future scenario with quantum computing.
-
In addition, the solution fully complies with the requirements of ISO 24745, the standard that governs biometric information protection.
Secure storage and homomorphic encryption
Biometric vectors are stored using homomorphic encryption to ensure the security and privacy of the data.
Homomorphic encryption allows biometric operations to be carried out directly on encrypted vectors, without ever having to decrypt them. This ensures that the original biometric vector is never exposed, safeguarding the process at all times.
As a result, vectors remain encrypted in the database, with each client assigned a dedicated encryption key that is securely stored in a separate secrets manager. The spatial structure of the vectors is preserved, enabling biometric operations to be performed without decryption, thereby maintaining the integrity and security of the process.
Homomorphic encryption is the perfect complement to RBRs. While an RBR is already irreversible and revocable, adding homomorphic encryption means that comparisons are carried out in a fully opaque manner:
-
Traditional approach: the RBR or template would be decrypted in memory for comparison against a live capture → creating a potential vulnerability window.
-
With homomorphic encryption: both the stored template and the live sample remain encrypted throughout the process.
-
The biometric engine performs the comparison within the encrypted domain and produces a similarity score. Only the final result (match/no match) is decrypted.
This means that even if an attacker gained access to the system during verification, they would never obtain the original biometric data.
Protecting personal data with Mobbeel’s technology
Privacy lies at the heart of our development philosophy. To guarantee it, we employ state-of-the-art biometric modelling algorithms based on deep neural networks, fully aligned with the principles set out in ISO 24745 on biometric information protection (irreversibility, non-interoperability, and revocability).
Following the principles of Renewable Biometric References (RBRs), endorsed by the Spanish National Cryptologic Centre (CCN), we build robust authentication systems that provide the necessary inherence factor to confirm a user’s identity in both physical and remote environments.
To further reinforce security, we integrate homomorphic encryption into both the storage and processing of biometric vectors. This technology enables computations to be performed directly on encrypted data, without the need for decryption at any stage, ensuring privacy is maintained even during processing.
In addition, as part of our commitment to cybersecurity and compliance with ISO 27001, we implement advanced access control mechanisms to ensure that only authorised personnel can access critical systems.
Get in touch with our team if you’d like to set up robust identity verification mechanisms within your organisation.

I’m a Software Engineer with a passion for Marketing, Communication, and helping companies expand internationally—areas I’m currently focused on as CMO at Mobbeel. I’m a mix of many things, some good, some not so much… perfectly imperfect.




