Distrust. Anxiety. Impatience.
These are the most common emotions that a user experiences when facing a digital identity verification process. They are also the main reasons why many abandon the process before completing it.
Improving conversion in digital onboarding, especially during identity verification processes, is not only a matter of metrics. Above all, it is a matter of understanding. Knowing what the person feels, what inspires trust, and at what point drop-off occurs is just as important as any numerical indicator.
In this article, we will explore user psychology, UX design, and business strategies focused on fraud prevention, three pillars that can make the difference between a verification process that drives customers away and one that converts them into active users.
Definition of conversion rate in digital onboarding
In an identity verification process, the conversion rate is the key metric to measure and improve conversion in digital onboarding. It is defined as the percentage of users who start the process and complete it successfully.
Its simplest formula is:
Digital onboarding conversion rate (%) = (Users who complete the onboarding ÷ Users who start the onboarding) × 100
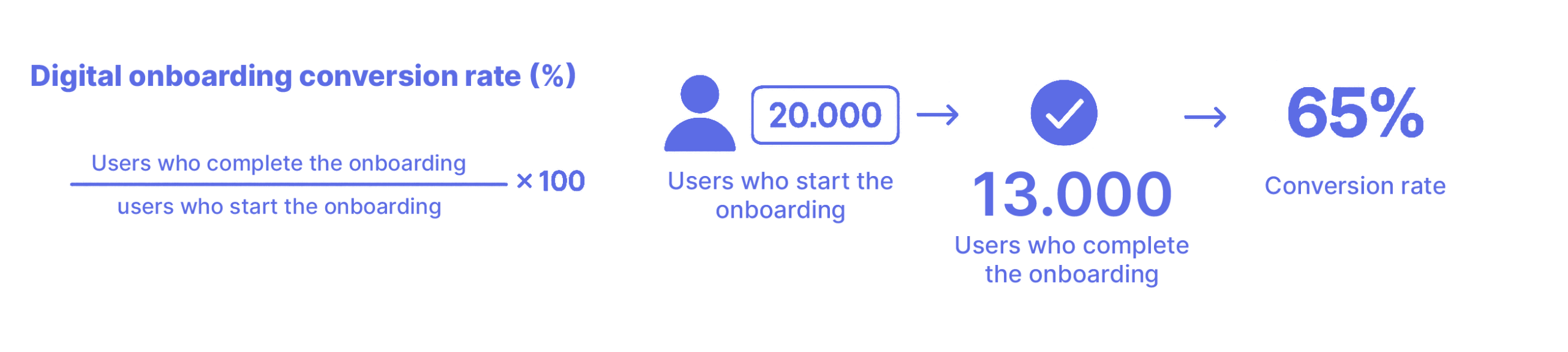
For example, if 20,000 users try to register in a financial app and only 13,000 complete the verification, the conversion rate will be 65%.
Beyond the number, the conversion rate works as a thermometer of the user experience.
- A high rate shows that the flow is clear, quick, and inspires trust.
- A low rate may indicate technical issues, excessive friction, or distrust at some stage.
Not all conversions are the same:
- Gross conversion: users who complete the process, regardless of whether they pass all controls.
- Effective conversion: users who complete it and are approved by fraud prevention systems.
The difference between the two reflects a constant dilemma: the tension between efficiency and security. A very high conversion can hide risks if fraud filters are too lax, while a very low one may suggest that legitimate customers are being blocked.
Psychological principles to improve conversion in identity verification
Applying cognitive and social psychology principles is essential to improve conversion in digital onboarding without compromising security. Classic models such as Cognitive Load Theory Sweller, or the cognitive biases described by Kahneman and Tversky explain why certain stimuli encourage users to continue while others trigger abandonment.

Trust and perceived security
Trust is the foundation of any relationship. According to the theory of perceived security in online environments, users do not act based on objective risk, but rather on their subjective interpretation of it.
- Trust signals: security seals and regulatory certifications.
- Representativeness heuristic: cognitive psychology shows that users often judge credibility by appearance. A consistent, professional design and well-written copy can inspire trust even before the user evaluates objective facts.
- Legitimising language: explaining clearly what data is requested, why it is needed, and how it is protected.
Reducing user anxiety
Identity verification naturally triggers some anxiety: activating the camera, taking a selfie, capturing a document… All of these steps raise doubts about control and what will happen to personal data.
Lack of information amplifies nervousness and increases the likelihood of drop-off. Reducing that feeling means anticipating the process and providing a sense of control.
- Process anticipation: showing a simple overview of the steps ahead and what is required to complete them successfully.
- Reassuring messages on data use and informed consent: explaining clearly how personal information will be used. Not through an unreadable legal text, but with accessible and transparent language.
- Control options: allowing the user to retake a photo if it is blurry increases willingness to complete the process.
Minimising cognitive friction
Each additional step in a verification process increases the likelihood of abandonment. Not because the user cannot complete it, but because every step adds cognitive load. When mental demand exceeds processing capacity, the likelihood of abandonment rises.
The user wants to think as little as possible. The interface should not appear complex, but rather guide users intuitively so that each step feels almost automatic.
Reducing this friction involves applying logical grouping of steps by breaking down the process into short blocks with clear, sequential screens.
Here the Hick-Hyman Law also applies: the more options presented, the longer the decision-making. Fewer buttons and fewer branches usually mean higher conversion.
The effect of social proof
The social proof effect explains why, in an identity verification process, users feel safer when they know others have successfully completed it before.
In uncertain contexts, we tend to imitate behaviour validated by the majority. This can be achieved through messages that display the number of verified users, include short testimonials, or feature logos of trusted partners.
How UX impacts conversion in digital onboarding
Designing experiences that reduce friction and make the process as intuitive as possible is fundamental to improving conversion in digital onboarding. Good design can also be decisive in preventing vulnerabilities and misuse. Some UX principles to consider are:
Mobile-first design
Most verification processes are carried out on a smartphone. A mobile-first design ensures that instructions are legible, buttons are accessible, and the camera functions without obstacles.
For cases where users begin on a desktop, it is advisable to offer a QR code redirection, allowing them to continue on mobile and return seamlessly to the desktop flow once verification is complete. This combines desktop flexibility with mobile simplicity.
Visual guidance during capture
Users should not have to guess what to do. On-screen frames, visual examples, and instant feedback help capture the document and selfie correctly, reducing the number of failed attempts.
Inclusivity and accessibility
Not all users have the same abilities, devices, or conditions. Designing with accessibility in mind means using clear language, ensuring compatibility with various devices, and adapt the experience to diverse user profiles.
In biometrics, factors such as disabilities, injuries, or even ageing can affect verification quality. To mitigate this, we use synthetic data to train and optimise models, ensuring fair and consistent performance for all users.
Our interfaces also comply with the WCAG AA international standard, ensuring accessibility and usability for individuals with diverse needs.
Balancing conversion and identity fraud prevention
There is no single formula. Everything depends on the specific context or scenario in which the technology is applied. To better understand this balance, it is helpful to examine two key aspects: a technical tool that enables rules and thresholds to be configured, and the practical application, which varies according to the sector, regulations, and objectives of each client.
Configurable validation matrix
Our solution enables the application of specific rules tailored to client needs through a fully configurable validation matrix.
This matrix defines thresholds and business rules that determine whether a process should be automatically approved, rejected, or flagged for manual review. This way, organisations keep control of the balance between conversion and security, adapting it to their operational and regulatory context.
The balance depends on the client’s scenario
Conversion rates in automated processes are influenced by multiple factors, including the client’s sector, the country’s regulations, and the specific details of the project.
This approach enables clients to tailor the process’s strictness to their specific context. For example:
- In high-value operations or highly regulated sectors, such as finance, strict verification makes sense, even at the cost of lower conversion rates, because security and compliance are the top priorities.
- In acquisition-focused registrations, such as online gaming, a fast and simple flow is more effective, even if the controls are less exhaustive.
Business strategies and key metrics in digital onboarding
The success of a digital identity verification process also depends on a business vision. To improve conversion in digital onboarding, it is essential to rely on metrics that show where to make improvements, justify strategic decisions, and demonstrate a return on investment.
Measuring drop-off rate at each step of the funnel
Knowing the overall conversion rate is useful, but not enough. The real value lies in analysing the drop-off rate at each stage of the funnel. For example, whether users abandon during document verification, facial biometrics, or final confirmation.
This analysis helps identify patterns, locate potential friction points, and prioritise optimisations with the greatest impact on success rates. Onboarding management thus becomes an iterative, data-driven process, rather than relying on intuition.
Data as a business lever
Beyond individual metrics, what matters is how they are used. Companies that integrate this data into their strategy can align conversion objectives with security and compliance goals, justify investments, anticipate risks, and accelerate growth on a solid foundation.
Contact us if you are looking to improve conversion in your digital onboarding with an industry-leading solution.

I am a curious mind with knowledge of laws, marketing, and business. A words alchemist, deeply in love with neuromarketing and copywriting, who helps Mobbeel to keep growing.

COURSE
The first COURSE on Digital Onboarding
Understanding the technology before implementing it ensures that you make the most of its potential and make informed decisions that benefit both your company and your end users.
We have developed a course that brings together everything you need to know about digital onboarding. This technology is the first point of contact with your customer and defines the course of your relationship.